Published: 2020.6.21
With the increase in digital surveillance, individuals have become more cautious about how they behave online as other parties can use one’s digital exhaust to tailor what a user sees or services they may qualify. Some members of the identity community have suggested using decentralized identity to reduce the risk of inappropriate data aggregation. Although most decentralized identity paradigms include some version of blockchain, an open, distributed ledger, the idea of a decentralized registry does not expressly require blockchain. A public key infrastructure (PKI) that includes payers as certificate authorities could support distributed identity in healthcare.
PKI is a paradigm that facilitates the creation, distribution, storage and revocation of digital certificates. These digital certificates are created with some mathematical wizardry that generates paired keys: a public key and a private key. Any information encrypted with one key must use the other key to decrypt it. PKI allows for parties who have never interacted before to exchange information securely.
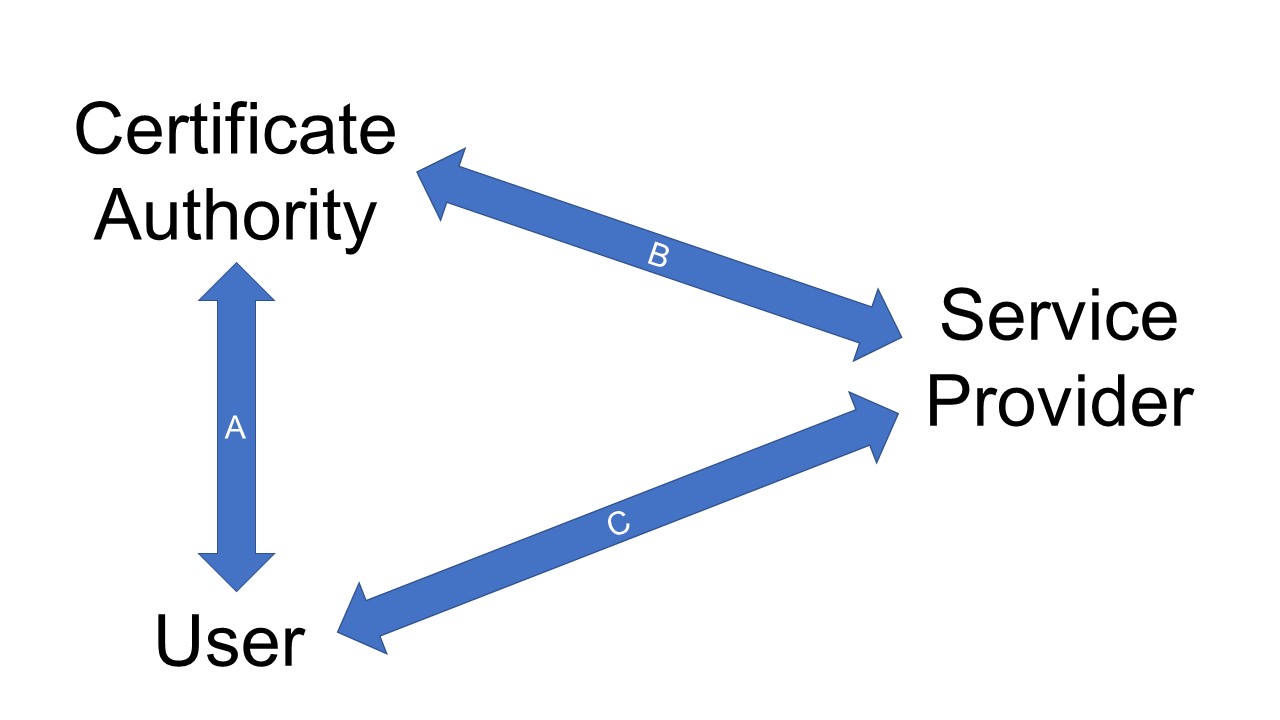
Figure 1. General public key infrastructure model
Figure 1 outlines how a public key infrastructure works. A certificate authority verifies that a user is who they claim to be (arrow A). The verification is up to the policies and procedures of the certificate authority. The National Institute of Standards and Technology (NIST) published digital identity guidelines to help organizations determine how best to establish one’s digital identity across three levels of identity assurance. When a user approaches a service provider (Arrow C), the service provider will want some level of assurance that the user is who they claim to be. The service provider might then contact the certificate authority to help authenticate the user (Arrow B). PKI allows the user’s private key to serve as one authentication factor. NIST published a separate set of authentication guidelines to provide guidance on how organization might best authenticate users with varying levels of confidence.
To address the challenge of a single certificate authority that might either use the knowledge of relationships between users and service providers or be at risk of having their system hacked to access those relationships, users should have the freedom to choose different certifificate authorities at will as even generate multiple certificates with the same certificate authority. As long as all participating certificate authority public keys (certificates) are available for review from a single central directory and all certificate authorities adhere to the same policies around identity verification and certificate maintenance, service providers and users should feel comfortable generating and using certificates from multiple certificate authorities.
Unlike other transactions, many American healthcare transactions include a payer, a provider and a patient. In many cases, the payer and the patient will pay some portion of the encounter cost. Even if the payer is not directly involved in addressing the care provided during a particular encounter, the payer may need to know how much the patient paid for the encounter to assign the cost toward the patient’s deductible. As long as the patient wants to use their payer affiliation to pay for services or receive a discount from the “sticker price,” decentralized identity may not make sense.
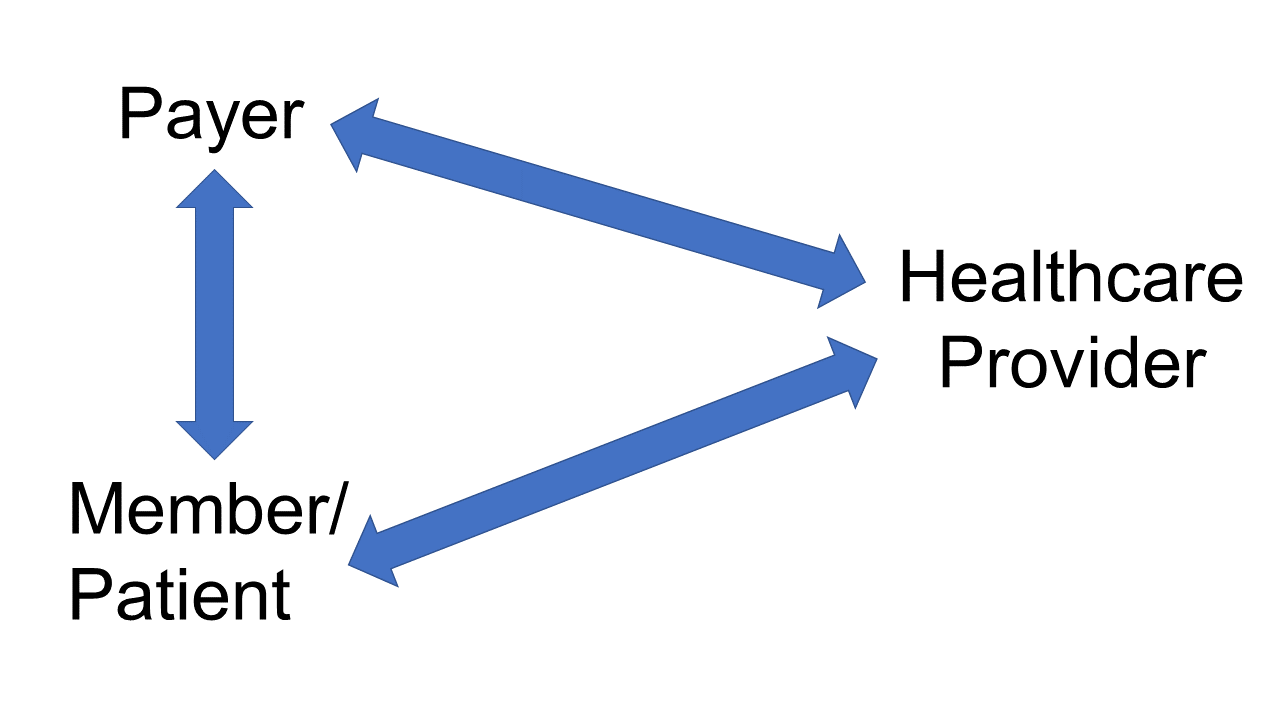
Figure 2. Payer as the Certificate Authority
If a payer served as a certificate authority (Figure 2), they could create multiple certificates for a specifific member, reducing the risk that an individual’s healthcare journey could be identified across different providers. Patients could use different certificate authorities when
- their health insurance changed, or
- they would like to perform a transaction unrelated to that health insurance company (e.g., self-pay).
Many healthcare entities would prefer to have a single identifier for all healthcare interactions. A single identifier would simplify data aggregation efforts and facilitate data sharing across different organizations. Fortunately, the decentralized identity model allows individuals to use a single identifier for all of their transactions, healthcare or otherwise. Our current experience with data breaches across multiple business sectors supports the contention that a more flexible identity paradigm may be required moving forward. This depiction of a decentralized identity paradigm moves the healthcare system one step closer to a marketplace where individuals might be able to generate their own key pairs with multiple certificate authorities to reduce the risk of third parties assembling a patient’s complete longitudinal health record based on digital surveillance.
*Dislaimer: I am currently the chair of the board of directors for DirectTrust, a nonprofit supporting companies use a PKI to transmit personal health information over email securely.